And as we all prepare for our final days off before year-end, before signing out for annual pie-making contests and cookie-baking (and eating) marathons, there’s one more item that we must check off…
Amidst the good cheer, a group lurks, waiting for us to let our guards down. The busier we get, the easier it is for malicious threats to get past our usual diligent selves.
Why do hackers strike more during the holiday season?
- Increased financial and email activity = more chances for hackers to strike.
- We’re so busy trying to get the last tasks done that we’re working faster, and maybe being a bit less diligent.
- It’s the season of giving! Of course our guards are lower! (And unfortunately, hackers know and take advantage of that fact.)
Here are three ways to ramp up your security policies—at work and at home—to stay safe and secure and avoid a successful cyberattack.
Security tip 1: Check your passwords and passphrases
Ensuring you have a strong, sufficient password is the first step to securing … everything! Here are a few good rules of thumb when creating passwords—check to ensure that you’re using these rules across every account.
Secure passwords are:
- 12+ characters long
- A mix of words forming a sentence (known as a passphrase)
- Unique, never repeated across accounts
Security tip 2: Enable multifactor authentication
Layer strong passwords and passphrases (like the ones described above) with multi-factor authentication applications and immediately gain an extra layer of security. We use the multifactor authentication application Duo at Rightworks (we also include it in every cloud hosting package.) With Duo enabled, each time I log into an application, Duo pings me, asking if I’m *actually* the one attempting to log into my account.
For example, let’s say I’m logging into Outlook:
- First, I enter my username and password/passphrase.
- A screen pops up on my computer, asking how I’d like to verify my identity.
- After selecting my preference, I open my phone and verify that, yes, it really is me trying to log in to work at 7:43 a.m.
That’s it!
The whole process takes an extra 10 seconds, and from those steps, it’s clear that even if a hacker were able to guess my extremely unique, long passphrase, they would not be able to proceed to the next step.
Security tip 3: Slow down
Yea—a bit backward-seeming advice, right? But the numbers speak for themselves. And all of the password, security, multifactor authentication technology in the world cannot protect you from yourself.
“Human error was a major contributing cause in 95% of all breaches. In other words, had human error not been a factor, the chances are that 19 out of 20 breaches analyzed in the study would not have happened at all.” Hacker News
Hurts, doesn’t it?
Here are some tips to use when browsing through your inbox, internet, etc. When sorting through email, pay attention to:
- The sender
- The sender’s email address
Look at the email address domain. Look at the naming convention preceding the email address domain. If a) you don’t recognize the sender, b) the sender usually communicates from a different email, or c) the domain is off, these are all signs that a hacker may be trying to get you to take the bait.
Here’s an example, using my email address:
- Correct email: kwilliams@rightworks.com
- Incorrect email: k.williams@right-works.com
- Incorrect email: kwilliams@rightw0rks.com
- Incorrect email: kwilliams@rghtworks.com
At first glance, the last three could pass as my legitimate email address. And at the fast pace we all work, a user could see one of those, scan over the contents, and open up whatever attachment or link “I” have sent them.
It’s only by slowing down and reading who the email is coming from that a user would notice the slight variation and raise the red flag.
Stay attentive. Slow down. Do not fall for common hacker tricks. Verifying the sender’s email address is legitimate is only the first step—unfortunately.
Look out for these other red flags:
- Bad spelling and grammar
- A sense of urgency
- Threatening language
- Unrealistic promises
- Unexpected attachments
- Suspicious links
Here are a few examples of these hacker tricks in action.
Phishing example 1: Urgency, bad grammar, unexpected
The founder and former CEO emailed me, requesting that I take care of an urgent matter. We’ve never spoken before, so that immediately raised a red flag. The lack of subject line, poor grammar and urgency raised more red flags. And what the “urgent matter” actually was? No one knows because the hacker wasn’t smart enough to come up with something:

Phishing example 2: Suspicious links
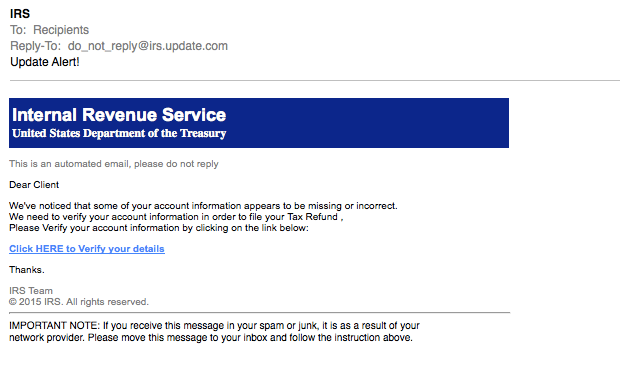
The IRS asks me to verify some information before they can process my return. The IRS is a big fan of snail mail and would never request PII via email link, so again, hacker—be better at what you do. (Note the obvious sarcasm.)
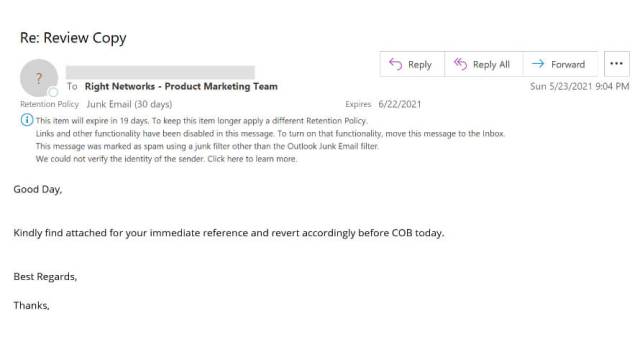
Phishing example 3: Unexpected attachment, urgency, bad grammar, sent to the entire department
Here’s another red flag: If something is sent to an entire team of people—but is clearly something one person would take care of—something’s off. The hacker is attempting to get as many individuals to click or open the malicious file; the attempt is poorly executed, because everyone on my team is well aware of such trickery. Note who the email was sent to and what the directions state.
Protect from cyberthreats with cloud security
What did we learn? In conclusion:
- Use strong, 12+ character passwords or passphrases
- Enable multifactor authentication
- Slow down and pay attention
Of course, there’s one more way you can ensure secure, safe browsing and email-checking: Use the cloud.
Rightworks’ suite of cloud solutions make applications, software, and data accessible in real-time from any device—plus, we’ve equipped it to recognize and neutralize cyberthreats.
Schedule an appointment to learn more about the security benefits that our cloud solutions provide firms and businesses today.

